What’s past is prologue – Critical Comms Today
Video Interview: Can We Make A 6G That Users Want?

6GWorld spoke with William Webb, CTO at Access Partnership and former CTO of OFCOM, about the institutional barriers standing in the way of making the next generation of networks a commercial success… and how to overcome them.
Toward Efficient Vertical Industries in B5G/6G Era: Technical Aspect and Standardization Directions – ITRI

he research and development community globally has nearly completed the design and specification of architectures, protocols, and mechanisms aimed at fulfilling the diverse and stringent requirements for the realization of a new network generation. It is now crucial that this technology is put into action in real-life trials to validate and demonstrate its value proposition for the vertical industry.
ITU WORKSHOP ON “IMT FOR 2030 AND BEYOND” – June 14th Presentations
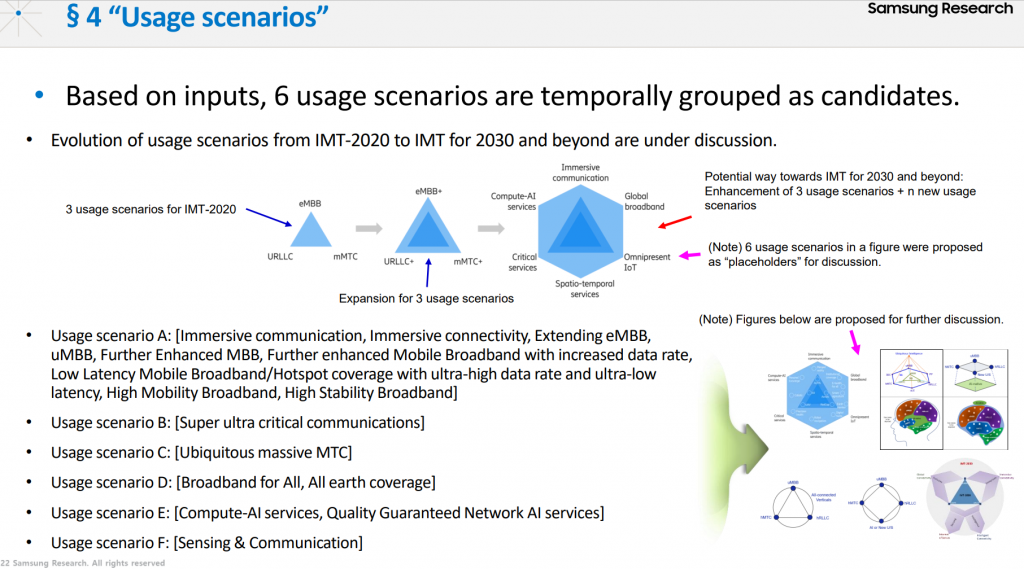
On June 14th a select group of global stakeholders shared their visions to feed into the ITU’s plans for what the next generation of telecoms should look like. While attendance was strictly limited, the presentations shared are available on the meeting website, linked here.
ETSI – MEC Security White Paper: Status of Standards Support & Future Evolutions

This White Paper, the very first initiative in this domain, aims to identify aspects of security where the nature of edge computing leaves typical industry approaches to cloud security insufficient.
Edge computing environments are characterized by a complex multi-vendor, multi-supplier, multi-stakeholder ecosystem of equipment and both HW and SW devices. Given this overall level of system heterogeneity, security, trust and privacy are key topics for the edge environments.
In this heterogeneous scenario, end-to-end MEC security considers the impact on the elements coming from all stakeholders involved in the system. The paper provides an overview of ETSI MEC standards and current support for security, also complemented by a description of other relevant standards in the domain (e.g. ETSI TC CYBER, ETSI ISG NFV, 3GPP SA3) and cybersecurity regulation potentially applicable to edge computing. The White Paper concludes on a general perspective of future evolutions and standard directions on MEC security.



