Guest Post: Navigating the IoT security landscape

Security and resilience in the telecoms landscape will only increase in significance over time; within that, managing security for the vast array of IoT devices and systems in all their diversity is a particular challenge. In this guest post, Wireless Logic’s Iain Davidson explores ways forward driven by legislative pressure.
From Security-Enhanced 5G Systems to Security-By-Design 6G Systems – Rakuten Symphony

In this white paper, Dr David Soldani explores the differences between security and privacy integration in 5G and 6G, outlining how the two generations differ and also makes some practical recommendations for how to pursue the development of secure telecoms today.
Towards Dependable 6G Networks – TechRxiv
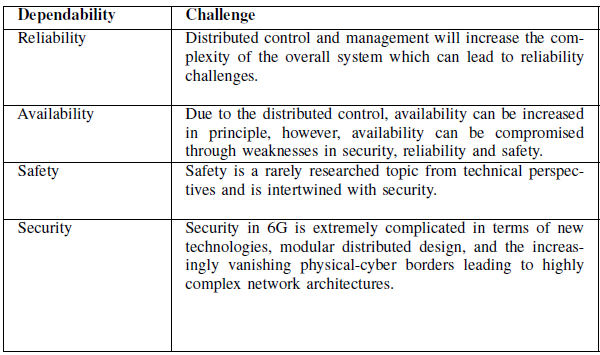
6G communication networks must be highly dependable. We take four dependability concepts such as reliability, availability, safety and security, and discuss the dependability of 6G networks. This
article, in summary, provides interesting insights into existing
challenges and advocates future research through highlighting
the most important research directions to make 6G dependable.
Securing ArtificiaI Intelligence (SAI); The role of hardware in security of AI – ETSI
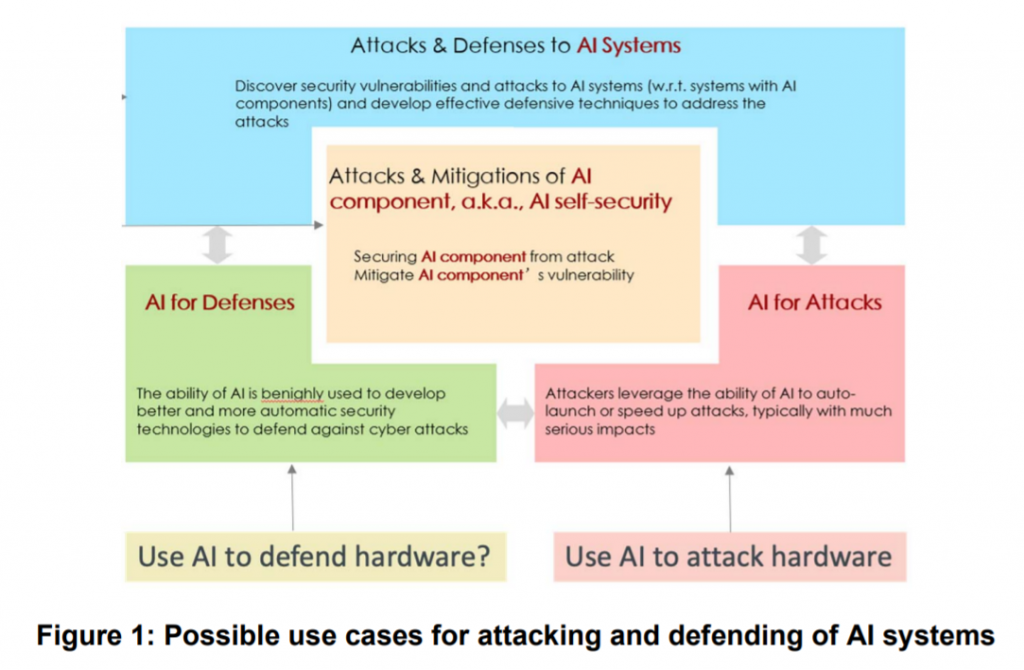
ETSI’s newly published report gives an overview of the roles of general-purpose and specialized hardware, such as neural processors and neural networks, in enabling the security of AI. The report identifies hardware vulnerabilities and common weaknesses in AI systems and outlines the mitigations available in hardware to prevent attacks, as well as the general requirements on hardware to support the security of AI (SAI).
6G Fundamentals: Vision and Enabling Technologies – David Soldani
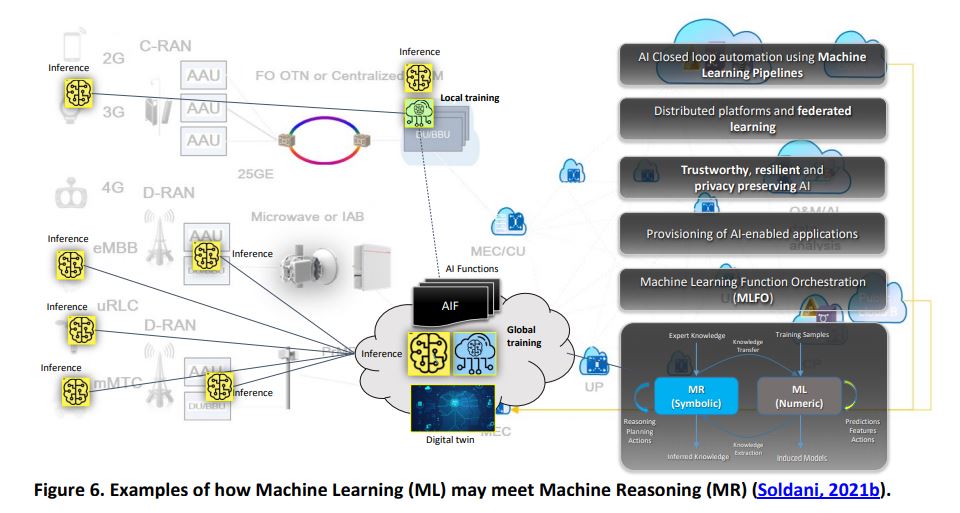
This research article, published in the “Journal of Telecommunications and the Digital Economy”, covers off some of the key elements for 6G’s development, including elements such as security by design.



